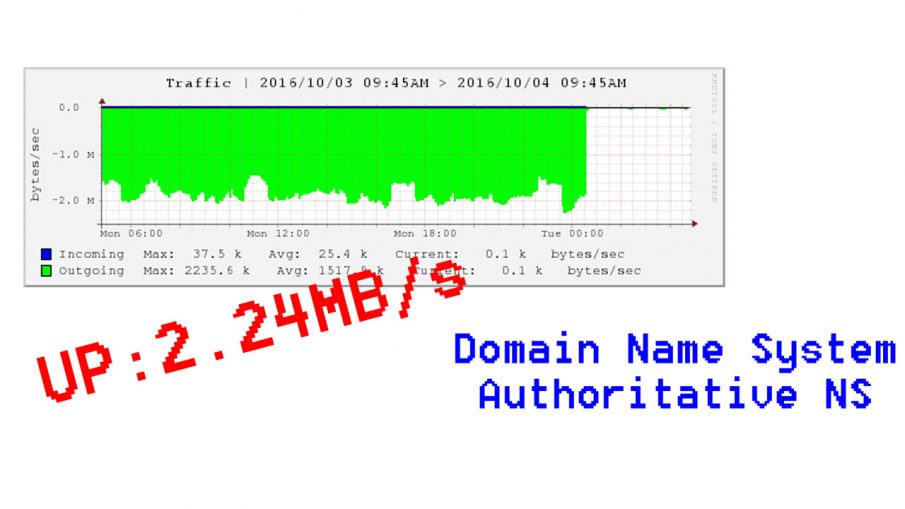
A DNS amplification attack is a type of Distributed Denial of Service (DDoS) attack that uses a DNS server to send large payloads to a target server with intent to overwhelm the target server.
The attacker will spoof the IP address of the target server and send a very small DNS query to a DNS server. The query could just be an ordinary request sent rapidly or it may be a query of type ‘ANY’ that requests an entire DNS zone.
This problem is more likely to occur if your DNS server is an Internet/Cloud server that is authoritative for one or more domain names. There are security practices that you should apply to your servers and one that you must do to prevent significant bandwidth loss:
On a Red Hat server in ‘/etc/named.conf’:
options {
recursion: yes;
}
The text in bold refers to recursive DNS lookups, this means if your server doesn’t contain a zone then it will lookup the zone on another DNS server. Your options are to either disable it or lock it down to specific IP addresses using something like “allow-recursion: { 10.0.0.1; };“.
It’s also advisable to lock down other functions like zone transfers, but you will have to keep queries open for it to actually resolve domain names to IPs.

Leave a Reply